When you install Oracle Entitlement Server (OES) and login to OES Policy Administration Console (http://WebLogicAdminHost:AdminPort/apm), you use user weblogic created during OES domain configuration. OES by default uses WebLogic’s Servers embedded LDAP Server to login to OES Administration Console (/apm). This post covers steps to integrate OES with external LDAP server (OID) so that user in OID can login to OES Administration Server console (APM) to define/manage policies & configuration.
High Level Steps to integarte OES wth OID (LDAP) Server
- Create user/group in OID (LDAP) that will be used to manage OES Administration Server console
- Add OID as Authentication Provider in WebLogic Server hosting Oracle Entitlement Server (OES)
- Map OES Application Role systemAdmin to OID (LDAP) group created earlier
- Test access to OES Administration Console (/apm) by login as OID (LDAP) user
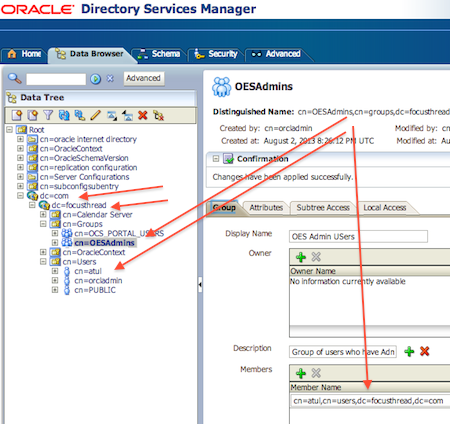
1. Create User & Group in OID:
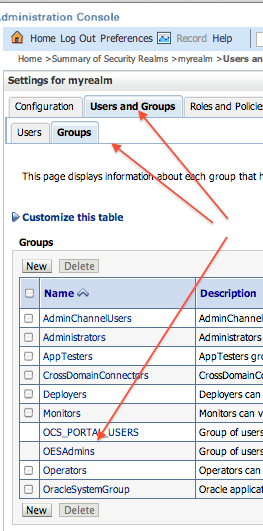
First step is to create user (In this example I created user atul), group OESAdmins, and add user (Atul) as member of group OESAdmin. Use ODSM or command line tool ldapadd to create user and group
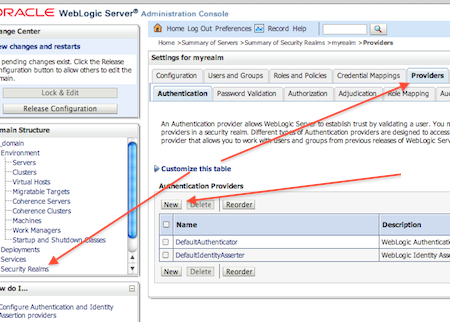
2. Add OID as Authentication Provider in WebLogic Domain hosting Oracle Entitleemnt Server.
Use steps mentioned here to add OID as additional Authentication Provider in WebLogic .
Note the following points
- Ensure that Control Flag (JAAS Flag) is set to SUFFICIENT for default authentication, OID Authentication or any other authentication provider configured in Security Realm of WebLogic Server where OES is deployed
- OID Autheticator as first autentication provider (or add property virtualize with value true to file $DOMAIN_HOME/config/fmwconfig/jps-config.xml)
Note: If OID is not first Authentication Provider then users & groups from OID will not be available in OES administration console
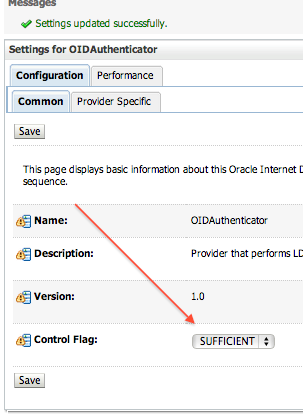
- Change Control Flag for OID Authenticator and Default Authenticator to SUFFICIENT
- Update following properies of OID Authentication Provider specific configuration
Host : hostname where OID is running
Port : OID listen port
Principal : DN of the user connecting from OES server to OID to extract users/groups (I am using cn=orcladmin)
Credential : Password of user used above
User Base DN : container from which users are retrieved and authenticated for OES (In my case value is cn=Users, dc=focusthread,dc=com)
User From Name Filter : change cn to uid (or mail) (This is the username user will use to login to OES Administration Console)
User Name Attribute = uid (or mail) (This is the username user will use to login to OES Administration Console)
Group Base DN = container from which Groups are retrieved and authenticated for OES (In my case value is cn=Groups, dc=focusthread,dc=com)

- Reorder the Authentication Provider and make OID as first authentication provider
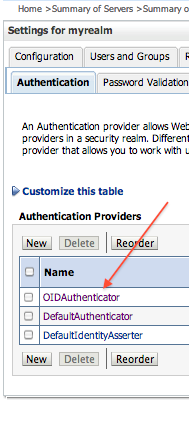
- Save the changes and restart WebLogic Server where Oracle Entitlement Server is installed
- Login to WebLogic Console and ensure that you can see OID Users and Groups : Security Realms -> myrealm -> Users and Groups
3. Map OES Application Role to OID Group
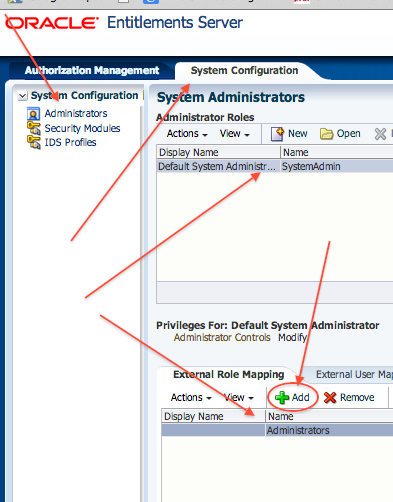
- Login to OES Console as user Weblogic and then System Configuration -> Administrators
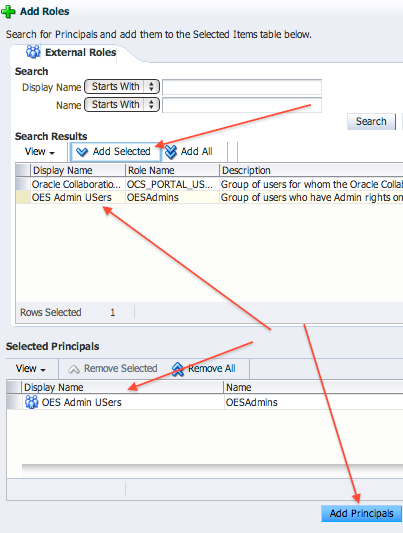
- Select Role SystemAdmin and click on Add on External Role Mapping
Note: If you want to see embedded WebLogic Groups then follow below workaround
____
Add below entry to $DOMAIN_HOME/config/fmwconfig/jps-config.xml
<property name=”virtualize” value=”true”/>
to the section
<serviceInstance name=”idstore.ldap” provider=”idstore.ldap.provider”> <property name=”idstore.config.provider” value=”oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider”/> <property name=”CONNECTION_POOL_CLASS” value=”oracle.security.idm.providers.stdldap.JNDIPool”/> </serviceInstance>
It shoul look like this:
<serviceInstance name=”idstore.ldap” provider=”idstore.ldap.provider”> <property name=”idstore.config.provider” value=”oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider”/> <property name=”CONNECTION_POOL_CLASS” value=”oracle.security.idm.providers.stdldap.JNDIPool”/> <property name=”virtualize” value=”true”/> </serviceInstance>
____
4. Test OES/OID Integration
- Login to OES Administration Console using user in OID who is member of Group (OID) which is mapped to OES Application Role SystemAdmin
.
Related/References