Is your Single Sign-On (AS-SSO) Server revealing too much information ?
Without going too much into write-up, lets evaluate Oracle’s own implementation of Single Sign-On Server i.e. https://login.oracle.com (In use by application like OTN, Conference.. )
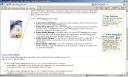
Server Name & Identity Management Version
If you check screen shot (Oracle’s Login Server i.e. https://login.oracle.com), you can figure out that
- Login server (Single Sign-On Server) is using Oracle Identity Management (10.1.4.0.1)
- This is deployed on server rexweb100.oracle.com (+ other middle tier in cluster) with enterprise manager console running on port 1810
.
Users details from OIDDAS
Now login to Oracle’s DAS (Delegated Administrative Services) using https://login.oracle.com/oiddas on top right of page click on Login page , you can login with your OTN (Oracle Technology Network) account or create new account (using yahoo, gmail or any valid email address)
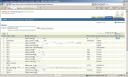
After login; click on Directory tab and from this screen any user could search for details of other user including their email address (Check screenshot) – Useful for spammers or marketing team to target email address directly
.
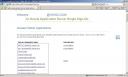
Partner Application in SSO Server
To list all Partner Applications registered against login.oracle.com check URL https://login.oracle.com/sso
.
Don’t you think Oracle should hide user details (specially “email address” attribute) from OIDDAS search screen ?
If you are SSO/OIDDAS administrator, What would you do in DAS configuration to hide listing email address or protect other SSO details (leave your views as comments) ?
Stay tuned to find out how to hide above information from users….
About the Author Atul Kumar
Oracle ACE, Author, Speaker and Founder of K21 Technologies & K21 Academy : Specialising in Design, Implement, and Trainings.